 Rabu, 26 Februari 2025 (23:30)
Rabu, 26 Februari 2025 (23:30)
 Music |
 Video |
 Movies |
 Chart |
 Show |
 |
SearchSploit Guide | Finding Exploits | Kali Linux (Cyber Opposition) View |
 |
SearchSploit - Searching For Exploits (HackerSploit) View |
 |
Finding Exploit using searchsploit on Kali Linux (AN1InFo) View |
 |
Metasploit For Beginners - How To Scan And Pwn A Computer | Learn From A Pro Hacker (Loi Liang Yang) View |
 |
Search For Any Exploit in Kali Linux with SearchSploit and ExploitDB (HydronicX) View |
 |
Manual Vulnerability Analysis Searchsploit (exploit) View |
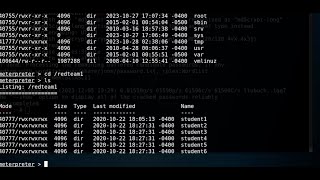 |
How to exploit port 80 HTTP on Kali Linux (CreatyR) View |
 |
SearchSploit - Searching For Exploits | SearchSploit Guide | Finding Exploits | Kali Linux (Technical Khan) View |
 |
Demonstrating how Hackers search for exploits and Launching an attack with metasploit (StealthyCyberTaco) View |
 |
Exploit Searching and Ethical Hacking with Searchsploit (Ian Trimble) View |